With the rise in the use of computer technology in the
supply chain, the piracy of intellectual property has also increased significantly. Because many companies supply
chains span many countries, checking to make sure that companies are impinging
on these intellectual property claims can be a real challenge. In
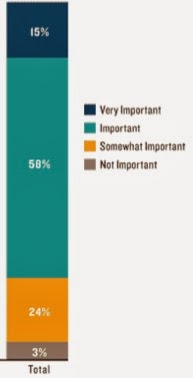
recent PwC State of Compliance 2013 Survey, manufacturing companies ranked
intellectual property as one of their top three risks facing them in today’s
marketplace. Moreover, 52% considered trade secret theft the greatest IP risk.
Source: http://www.ism.ws/files/images/Pubs/091130_b.gif
The scariest thought about the whole
mess is that the countries that are breaking IP laws are those that provide a
great deal of our supplies. According to a White Case research paper, seven of the top twenty countries for pirated
software sales are in Asia, and China is the
number two country globally on this list, with an estimated 77% of its software pirated. The most difficult
part is that these organizations are so incredibly far away that doing monitoring
of IP infringement can be very difficult. This threat has real implications on supply chains and the
companies that hold them. In October of last year, Citi agreed to pay fines of
$30 million after its analysts leaked information on Apple's iPhone supply chain
to a number of big clients.
Broad Look at Applications to Supply Chains
Although piracy and counterfeiting of
intellectual property is a hug concern, for the sake of this blog, I’m going to
focus specifically on technology in the supply chain. I will advocate that
companies all get on the same supply chain software to cut down on intellectual
property infringement. I think that this will kill two birds with one stone:
increasing data to help in lean supply chain practices and ensuring compliance
with IP laws.
If everyone is using the same software,
it should theoretically be easier to make sure it’s all legal goods. You should
be able to check with software retailers to make sure that what your
subcontractors are using is registered and legal. Tangentially, if retailers
are using a specific type of software, there is a good chance that they will
need to have other products associated with these goods (such as barcode
scanners, tablet computers, or other pieces of information).
You should be able to set up automatic
systems to inform you when subcontractors have ended contracts, when contract
periods have expired, or when you are missing information about their systems.
Businesses neeed to accept the fact
that expenses will rise when companies are all in compliance. Some of these software
packages will have hefty costs, and that will trickle down to more expenses for
you as a company. Yet, it should outweigh the inevitable future risk of
lawsuits.
You also may loose suppliers when you are working out your
system. The cost and the complication of implementing a system may be too much
for your supplier. Try to negotiate with the supplier, but from the beginning
prepare alternate suppliers for all of your products so your not left in the
lurch if someone backs out.
There are many great resources out
there on actions you might take, and I’ve compiled what I think to be the most
useful suggestions.
How to Find IP
violations
Audit Your System:
It may be difficult to track down the violators in your supply chain, but
having a clear plan to track compliance and build protections into new
contracts is essential. The most
important thing to do is initially audit your supply chain. Where are the
weaknesses in your system, and who do you have contracts with to protect
yourself?
Establish Groups to
Monitor: You should require that all sub-contractors allow you access to
their facilities and their offices and keep records of their compliance.
Develop a branch of your organization that monitors compliance. Invest in
technology to help you be complaint in the process as well.
Source: ipo.gov.uk
What Happens if you
Do Find Infringement
From everything I’ve seen, the best
advice would be to report it to the proper authorities and get their advice.
Make sure that you are on the right side of the law, and show your good faith
by reporting it as soon as you find out. Figure out with the authorities what
the proper course of action is to move forward. The Whitecase Report I cite has
many instances on leniency granted to organizations who’ve come clean to the
authorities. The problems seem to come when organizations try to deal with it
internally and keep it under wraps for extended periods of time.
How to Make Sure it
Doesn’t Happen Again
Find Good Lawyers
In-Country: Have good counsel from someone who is in that country so that
you can evaluate how best to implement a contract. The best route may vary from
country to country, so you may need to try different approaches with different
sub-contractors.
Make New Contracts: Start
from scratch if you have to, but get new contracts into the system. Cover
yourself and make sure that you have the contracts in place.
Other things you want to consider
doing:
-
Ongoing Education for Company and
Suppliers
-
Join Trade Groups to Keep Abreast of
Trends and Suspicious Practices
-
Publicize your Policy with Industry
Groups
-
Take the Lead in Establishing
International Guidelines
Unresolved Questions
After researching the topic, I want to pose a few questions:
what do you think the
future of international IP guidelines will be?
Can we ever make it to the point where we can create an enforceable
international system?
What kind of insurance do organizations need to have in
response to hackers and online data breaches, and will they have to carry this
insurance for their suppliers and subcontractors as well?
Sources:


this is really a great blog...........
ReplyDeleteSCM Real Estate Solutions